Odoo CE in Azure

I’ve been interested in Point of Sales systems for a while now, mainly as my parents own a mini mart that I believe would benefit from having a modern POS solution. Odoo caught my eye when browsing the azure marketplace with images packaged by bitnami. I was very pleased at what Odoo had to offer it did everything I needed it to do and more. The image packaged on the marketplace was the enterprise edition, which meant I ran into some issues when configuring the application as I did not have the appropriate license. That’s when I found the community edition which resolved all of my issues. In this article I’ll walk you through how I deployed both the infrastructue and the application using a combination of technologies I’ve learnt over the past few months.
In order to deploy my solution I’d first have to stand up a VM in azure. As I’m currently learning terraform I took the opportunity to use terraform to deploy the virtual machine I’ll be using for this project. The resources I deployed for this project included: A Resouce group A Standard B1ms azure virtual machine An OS disk A NIC A Public IP - Dynamic A Network Security Group A Subnet A Virtual Network
As I did not deploy a vpn gateway for this project this meant I would be directly interacting with my machine through the public IP; definitely not an ideal solution for a system in production. For this project I had to allow inbound traffic to port 8069, which is odoo’s default port for the web UI, on my Network Security group. Port 8069 was then closed after enabling ssl, I then allowed inbound traffic to ports 80 and 443. Port 22 was also opened as it was necesary for sshing into my virtual machine. The specific rule I set for port 22 only allowed inbound traffic from my public IP address. Idealy with a VPN Gateway I would be able to change this to my private IP address instead of my public IP address.
Odoo recommends a 2 core 4GB Ram machine but I found for my purposes a Standard B1ms machine with a single core and 2GB of ram worked well for me.
After deployment in azure I began by sshing into my virtual machine and running:
sudo apt-get update && sudo apt-get upgrade
Before we install Odoo erp, we need to install postgresql, which the only prerequiste for Odoo.
Postgress is easily installed by running
sudo apt install postgresql -y
We can then install Odoo Community Edition
The first thing we do is get the key for the official Odoo repository
wget -qO- https://nightly.odoo.com/odoo.key | gpg --dearmor | sudo tee /usr/share/keyrings/odoo-key.gpg
We can then add the Odoo repository to our aptitude sources
echo "deb [signed-by=/usr/share/keyrings/odoo-key.gpg] http://nightly.odoo.com/15.0/nightly/deb/ ./ "| sudo tee /etc/apt/sources.list.d/odoo-key.list
We can then update our repositories using
apt-get update
Then install Odoo
apt-get install odoo
After Odoo is installed we can access the Web UI on port 8069
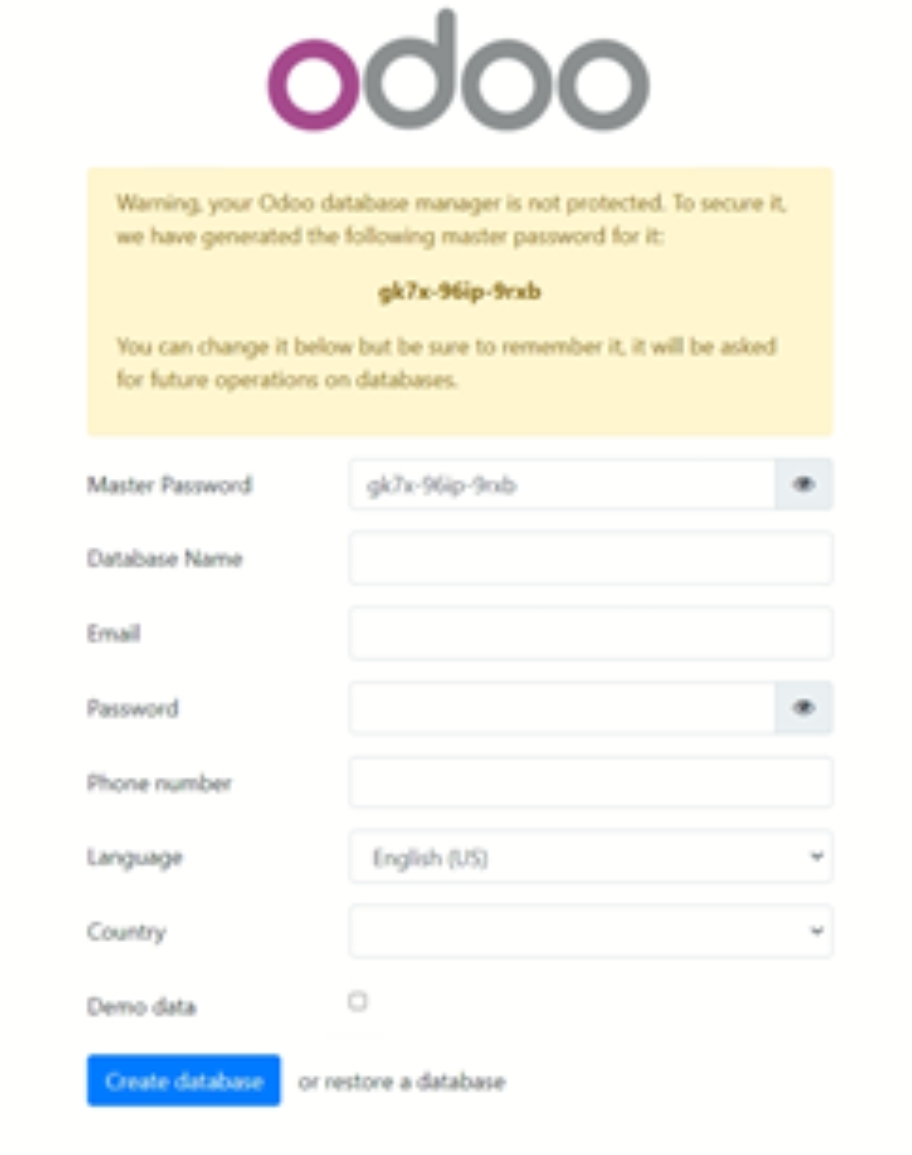
At this point Odoo is practically ready to use; however there’s a few things we can do to make this solution ready for a production environment. The next few steps goes over how I generated some ssl certificates and ensured that all our traffic was encrypted
Install nginx and stop the service
sudo apt-get install nginx
sudo service nginx stop
Port 80 needs to be free for us to generate the letencrypt certificated with certbot. This is why we stop nginx or any other services that may use port 80.
We can use certbot to generate ssl certificated that will ensure for more secure connection
First install certbot by running
sudo apt-get certbot
Then generate certs by running.
sudo certbot certonly --standalone -d <your.domain.com> --preferred-challenges http --agree-tos -n -m <your@email.com> --keep-until-expiring
The ssl cert and cert key is normally stored in the /etc/letsencrypt/live/yourdomain/ directory
Now that we’ve got our certificates we can enable ssl, for this i’m following the odoo documentation.
in /etc/odoo/odoo.conf set:
proxy_mode = True
if you dont have a odoo.conf file make one:
sudo vi /etc/nginx/sites-enabled/odoo.conf
in /etc/nginx/sites-enabled/odoo.conf set:
#odoo server
upstream odoo {
server 127.0.0.1:8069;
}
upstream odoochat {
server 127.0.0.1:8072;
}
# http -> https
server {
listen 80;
server_name <yourdomain.com>;
rewrite ^(.*) https://$host$1 permanent;
}server {
listen 443;
server_name <yourdomain.com>;
proxy_read_timeout 720s;
proxy_connect_timeout 720s;
proxy_send_timeout 720s;
#Add Headers for odoo proxy mode
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
#SSL parameters
ssl on;
ssl_certificate <path to ssl cert>;
ssl_certificate_key <path to ssl cert key>;
ssl_session_timeout 30m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA';
ssl_prefer_server_ciphers on;
#log
access_log /var/log/nginx/odoo.access.log;
error_log /var/log/nginx/odoo.error.log;
#Redirect longpoll requests to odoo longpolling port
location /longpolling {
proxy_pass http://odoochat;
}
#Redirect requests to odoo backend server
location / {
proxy_redirect off;
proxy_pass http://odoo;
}
# common gzip
gzip_types text/css text/scss text/plain text/xml application/xml application/json application/javascript;
gzip on;
}
The last piece of this puzzle which isn’t strictly necessary but very important to have would be to allow Odoo to produce pdf documents. In order to print invoices or reciepts we’ll need the wkhtmlToPdf package. This can be installed by
wget https://github.com/wkhtmltopdf/packaging/releases/download/0.12.6-1/wkhtmltox_0.12.6-1.focal_amd64.deb
sudo apt install ./wkhtmltox_0.12.6-1.focal_amd64.deb
 This was a very rewarding project for me to complete, it really helped me to understand how far I’ve come and how much I’ve learnt about IT infrastructure over the last year. I’m able to use skills that I’ve learnt in my placement and skills that I’ve learnt on my own to develop a solution that, with a few added bits , I’d feel comfortable putting into a production environment.
This was a very rewarding project for me to complete, it really helped me to understand how far I’ve come and how much I’ve learnt about IT infrastructure over the last year. I’m able to use skills that I’ve learnt in my placement and skills that I’ve learnt on my own to develop a solution that, with a few added bits , I’d feel comfortable putting into a production environment.
Moving this solution into a production environment would involve proper networking, definitely adding an azure firewall. Adding virus protection in the form of clamav and a backup solution like azure backup or azure site recovery.
