Patching log4j Vulnerability in APC PowerChute Network Shutdown (PCNS) virtual appliances
On December 9th 2021 the log4Shell(CVE-2021-44228) vulnerability was publicly disclosed as a zero-day vulnerability in the log4j java logging framework. The vulnerability had the highest possible cvss score of 10/10, this meant long nights with a lot of patching and remediation work for IT professionals across the world.
I was tasked with remediating the log4Shell vulnerability on 9 APC PowerChute Network Shutdown (PCNS) virtual appliances. Not long after the vulnerability was disclosed Schneider Electric, parent company of APC, published an article detailing the steps necessary to remediate the vulnerability in their PCNS virtual appliances. It was a relatively easy fix however I had two main challenges.
- There were 9 machines and patching each machine one at time would simply take too long.
- There were firewall rules in place that stopped these machines from talking to the internet. I’ll explain why this was a challenge later on.
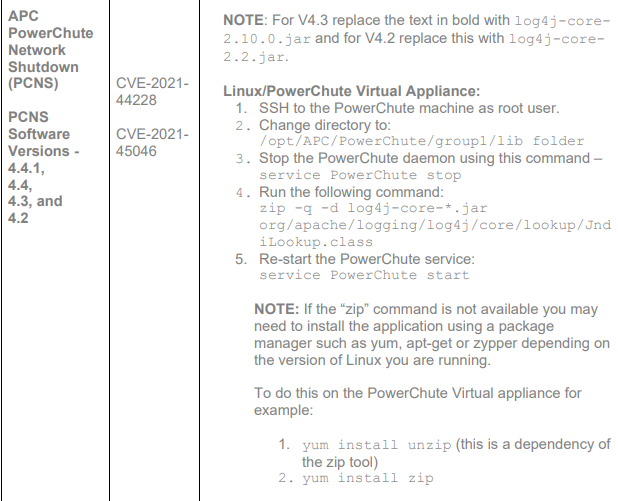
The remediation steps were as follows: link
We see here that the zip command was necessary to remove the jndilookup class from the compressed archive. These virtual appliances did not have zip installed so this package needed to be installed before any remediation work took place. As mentioned before the machines had no internet access so the .rpm packages had to be manually downloaded and installed using yum install . As these steps and the ones mentioned in the documentation were fairly simple unix commands, I decided to write my first ever Bash script that would execute all commands needed.
#!/bin/bash
echo "Installing unzip and zip"
yum install zip-3.0-11.el7.x86_64.rpm -y
yum install unzip-6.0-21.el7.x86_64.rpm -y
echo
echo "-------------------------------------------"
echo "CHECKING jdnilookupclass"
cat /opt/APC/PowerChute/group1/lib/log4j-core-*.jar | grep JndiLookup.class
echo "-------------------------------------------"
echo
service PowerChute stop
echo "removing class from zip"
echo "-------------------------------------------"
zip -q -d /opt/APC/PowerChute/group1/lib/log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
echo "-------------------------------------------"
cat /opt/APC/PowerChute/group1/lib/log4j-core-*.jar | grep JndiLookup.class
echo
service PowerChute start
You can download this script from my gitHub repository here
The first couple lines of the script would install the zip and unzip packages necessary to remove the jndilookup class from the .jar file.
The next two lines would then search for the JndiLookup class in the log4j java archive. After this is completed the remediation work starts as the following lines stops the PowerChute service and silently removes the class from the the java archive.
Once the class is removed I search the archive again to see if the class is still there and the PowerChute Service is restarted.
I copied this script along with the zip and unzip packages onto the virtual appliances via sftp, then used ssh to logon to the machines and run the script.
Overall I enjoyed doing this work as I feel comfortable in a Unix environment and I quite like scripting whether it be PowerShell or Bash.